doas groupadd vmail doas useradd -f vmail vmail doas mkdir /home/vmail doas chown vmail:vmail /home/vmail
Setup DNS A/MX record
mail.tomlab.jp A 160.251.6.214 tomlab.jp. MX 0 mail.tomlab.jp. ;;tomlab.jp. MX 10 mail-backup.tomlab.jp.
verify the settings by host(1) and dig(1)
host mail.tomlab.jp dig -t MX tomlab.jp +short
A large nuber of the hosts spamming the world do not have rDNS, do not have FCrDNS, or have an rDNS that matches a dynamically allocated IP pattern.
setup rDNS from provider's control panel.
Verify the records.
host 160.251.6.214 host mail.tomlab.jp
If they match both ways then everything's fine.
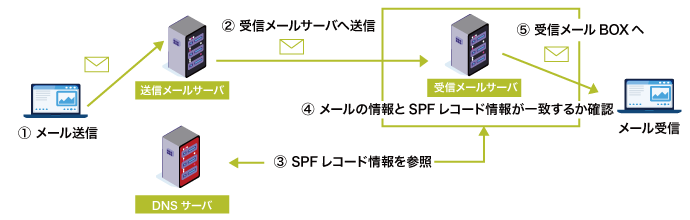
SPF は業界標準のメール認証方式である。
ドメインをなりすましから保護し、送信メールが迷惑メールに分類されないようにする。
SPFの仕様は、
RFC7208で規定されている。
SPF を使用して、ドメインに代わってメールを送信できるメールサーバーを指定する。
ドメインに設定できる SPF レコードは 1 つだけであるが、レコード中にはドメインに代わってメールを送信できるサーバーを複数指定できる。
受信側のメールサーバーは SPF を使用して、受信メールの送信元とされるドメインが偽装されたものではなく、承認済みのサーバーから送信されたことを確認する。
SPFレコード設定例
tomlab.jp. IN TXT "v=spf1 mx -all"
References:
Lack of DKIM has a very negative impact on the reputation of a domain.
2048 bits RSA public keys do not fit in a DNS TXT record and must be truncated into two records.
doas mkdir /etc/mail/dkim
doas openssl genrsa -out /etc/mail/dkim/tomlab.jp.key 1024
doas openssl rsa -in /etc/mail/dkim/tomlab.jp.key \
-pubout \
-out /etc/mail/dkim/tomlab.jp.pub
cat /etc/mail/dkim/tomlab.jp.pub
DNS TXT record
;; <selector>._domainkey.<domain>. ;; selector: whatever you choose, normally date 20221124._domainkey.tomlab.jp. IN TXT "v=DKIM1;k=rsa; p=PASTED PUBKEYSTRINGS.........."References:
RFC7489
_dmarc.tomlab.jp. IN TXT "v=DMARC1;pct=100;rua=mailto:postmaster@tomlab.jp;"References:
doas openssl genrsa -out /etc/ssl/private/tomlab.jp.key 4096 doas openssl req -new -x509 -key /etc/ssl/private/tomlab.jp.key \ -out /etc/ssl/tomlab.jp.crt -days 365 doas chmod 0600 /etc/ssl/private/tomlab.jp.key doas chmod 0600 /etc/ssl/tomlab.jp.fullchain.pem
doas cp /etc/examples/httpd.conf /etc/httpd.conf doas cp /etc/examples/acme-client.conf /etc/acme-client.conf
/etc/httpd.conf
server "mail.tomlab.jp" {
listen on * port 80
location "/.well-known/acme-challenge/*" {
root "/acme"
request strip 2
}
location * {
block return 302 "https://$HTTP_HOST$REQUEST_URI"
}
}
doas rcctl -f start httpd
/etc/acme-client.conf
domain mail.tomlab.jp {
domain key "/etc/ssl/private/mail.tomlab.jp"
domain full chain certificate "/etc/ssl/mail.tomlab.jp.fullchain.pem"
sign with letsencrypt
}
doas acme-client -v mail.tomlab.jpReferences:
Rspamd provides spam filtering methods, antivirus integration, and dkim signing.
Redis is used to store Rspamd statistics and greylisting state.
filter-rspamd allows OpenSMTPD to work with Rspamd.
doas pkg_add rspamd redis opensmtpd-filter-rspamd
Rspamd to handle my DKIM signing
doas mkdir /etc/rspamd/local.d
doas cat << EOF > /etc/rspamd/local.d/dkim_signing.conf
allow_username_mismatch = true;
domain {
tomlab.jp {
path = "/etc/mail/dkim/tomlab.key";
selector = "20221124";
}
}
EOF
doas rcctl enable redis rspamd
doas rcctl start redis rspamd
/etc/mail/virtuals
@ vmail
/etc/mail/credentials (root:_smtpd 0640)
smtpctl encrypt PASSWD
tom OUTPUT_OF_ABOVE_CMD
table virtuals file:/etc/mail/virtuals
table credentials file:/etc/mail/credentials
pki tomgena.com cert "/etc/ssl/tomgena.com.fullchain.pem"
pki tomgena.com key "/etc/ssl/private/tomgena.com.key"
filter "rdns" phase connect \
match !rdns \
disconnect "550 DNS error"
filter "fcrdns" phase connect \
match !fcrdns \
disconnect "550 DNS error"
filter "rspamd" proc-exec "/usr/local/libexec/smtpd/filter-rspamd"
listen on all \
port 25 \
tls pki tomgena.com \
filter { "rdns", "fcrdns", "rspamd" }
listen on all \
port 587 \
tls-require pki tomgena.com \
auth <credentials> \
filter "rspamd"
action "RECV" lmtp "/var/dovecot/lmtp" rcpt-to virtual <virtuals>
action "SEND" relay helo tomgena.com
match from any for domain "tomgena.com" action "RECV"
match from any auth for any action "SEND"
/etc/login.conf
dovecot:\ :openfiles-cur=1024:\ :openfiles-max=2048:\ :tc=daemon:
Remove all files
doas rm -rf /etc/dovecot/*
First, make an user file.
smtpctl encrypt PASSWD
format is user:password:uid:gid::homedir
In this guide, vmail user is used for all acounts,
so leave the uid, gid and homedir fields blank as below.
/etc/dovecot/users (root:_dovecot 0640)
tom:OUTPUT_OF_ABOVE_CMD::::
/etc/dovecot/dovecot.conf
ssl = required
ssl_cert = </etc/ssl/tomgena.com.fullchain.pem
ssl_key = </etc/ssl/private/tomgena.com.key
ssl_min_protocol = TLSv1.2
ssl_prefer_server_ciphers = yes
disable_plaintext_auth = yes
protocols = lmtp imap
service lmtp {
unix_listener lmtp {
user = vmail
group = vmail
}
}
service imap-login {
inet_listener imaps {
port = 993
}
}
passdb {
driver = passwd-file
args = scheme=BLF-CRYPT username_format=%n /etc/dovecot/users
}
userdb {
driver = passwd-file
args = username_format=%n /etc/dovecot/users
override_fields = uid=vmail gid=vmail home=/home/vmail/%n
}
mail_location = maildir:~/Maildir
dovecot -n rcctl enable dovecot rcctl start dovecot